On November 2,
The Guardian published a lenghty article about the Snowden-leaks, which said that besides the close intelligence-sharing group of the US, Britain, Canada, Australia and New-Zealand, known as 5-Eyes, there are also groups called 9-Eyes and 14-Eyes.
According to The Guardian, the first consists of the 5-Eyes countries plus Denmark, France, the Netherlands and Norway and the latter adding another five European nations. This caused some embarrassment, as especially France and The Netherlands were heavily opposed to NSA's eavesdropping operations.
For almost everyone the existance of these 'Eyes' came as a surprise, but as this article will show, there are also 3-, 4-, 6-, 7-, 8-, 9- and 10-Eyes communities. They were created for restricting access to military and intelligence information to respective numbers of coalition nations. These 'Eyes' are used as handling instructions and often supported by dedicated communication networks.
Many new 'Eyes'First we take a look at what
The Guardian wrote about the 9-Eyes and other intelligence-sharing groups:
"The NSA operates in close co-operation with four other English-speaking countries - the UK, Canada, Australia and New Zealand - sharing raw intelligence, funding, technical systems and personnel. Their top level collective is known as the '5-Eyes'.
Beyond that, the NSA has other coalitions, although intelligence-sharing is more restricted for the additional partners: the 9-Eyes, which adds Denmark, France, the Netherlands and Norway; the 14-Eyes, including Germany, Belgium, Italy, Spain and Sweden; and 41-Eyes, adding in others in the allied coalition in Afghanistan."
In a similar article,
The New York Times also mentioned these two new Eyes-groups, but without naming the participating countries, and instead of the 41-Eyes, adding NACSI, the NATO Advisory Committee for Special Intelligence:
"More limited cooperation occurs with many more countries, including formal arrangements called Nine Eyes and 14 Eyes and Nacsi, an alliance of the agencies of 26 NATO countries".
These new revelations seem to be confirmed by what is said in an informative 2012
paper (pdf) about Canada and the Five Eyes Intelligence Community:
"The Five Eyes sigint community also plays a ‘core’ role in a larger galaxy of sigint organizations found in established democratic states, both west and east. Five Eyes ‘plus’ gatherings in the west include Canada’s NATO allies and important non-NATO partners such as Sweden. To the east, a Pacific version of the Five Eyes ‘plus’ grouping includes, among others, Singapore and South Korea. Such extensions add ‘reach’ and ‘layering’ to Five Eyes sigint capabilities."
This text suggests that there are several western Five Eyes 'plus' groups, one of which sounds like the 14-Eyes mentioned by The Guardian. The eastern Five Eyes 'plus' refers to the 10-Eyes group, which will be described down below.
The existance of these hitherto unknown Eyes-groups came as a surprise, because it was generally assumed that NSA only had two kinds of partners for sharing signals intelligence:
-
2nd Party: the Five Eyes based upon the
UKUSA-Agreement of 1946
-
3rd Party: a range of countries that have bilateral agreements with NSA
The CFBL NetworkThe term 9-Eyes could already be found in some other sources. One is an extensive article by the French weblog
Zone d'Intérêt about the NATO exercise Empire Challenge 2008 (EC08), in which a number of operational and testing networks were used. One of them is the
Combined Federated Battle Laboratories Network (CFBLNet), which is for testing new ways of collecting and sharing intelligence, surveillance and reconnaissance (ISR) data.
The CFBL network consists of an unclassified (black) backbone network (the
Blackbone) with transporting the encrypted traffic of several classified and unclassified enclaves as its main purpose. The main secure domains on the CFBL Blackbone are:
- The
CFBLNet Unclassified Enclave (CUE), which is unclassified, but traffic is encrypted using Advanced Encryption Standard (AES) algorithms.
- The
Four-Eyes Enclave (FEE), which is a classified enclave at the SECRET level, accessible for USA, GBR, CAN and AUS only.
- The
9-Eyes or NATO Red Enclave, which is also a classified enclave at the SECRET level, accessible for the NATO members of the Five Eyes plus France, Germany, Italy, Spain, The Netherlands and Norway.
- The
Initiative Enclaves, which are created temporarily to support specific initiatives and are classified according to the initiative requirements.
We can see these parts of the CFBL Network mentioned in this slide about the networks used in the EC08 exercise:
![]() The various networks involved in Empire Challenge 2008 (EC08)
The various networks involved in Empire Challenge 2008 (EC08)
(COI = Community of Interest, CFE = CENTRIXS Four Eyes,
DDTE = Distributed Development and Test Enterprise)
(full presentation: EC08 Networks (pdf), May 2008)
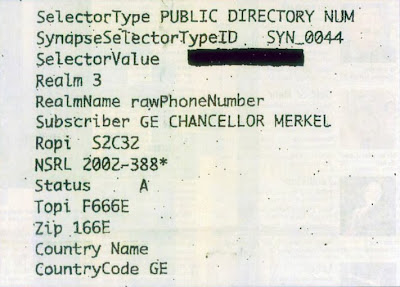
The 9-Eyes countries are also listed in a table in a NATO standardization
document (pdf) from 2010. There we see that from the 4-Eyes only the US, the UK and Canada are part of the 9-Eyes, which makes sense, as Australia is not a NATO partner:
This table lists the groups of nations to which some specific multi-national intelligence and reconnaissance information can be released. This is shown by using the
dissemination markings or handling instructions: REL NATO, REL 4-EYES, REL 9-EYES.
The famous Five Eyes term also has its origins in the former NSA dissemination marking EYES ONLY, which defined which 'eyes' may see certain material. Accordingly, documents authorized for release to the five UKUSA-countries were initially marked as AUS/CAN/NZ/UK/US EYES ONLY.
In conversations, allied intelligence personnel adopted the term "Five Eyes" as a shorthand because it was much easier to say. This term became widely used and even got its own abbreviation: FVEY, which is now used in REL FVEY, after the EYES ONLY marking was being replaced by the REL TO [country/coalition designator] format.
![]() A classification line showing the REL FVEY marking
A classification line showing the REL FVEY marking
If we compare the nine members of the CFBLNet NATO domain with the 9-Eyes countries mentioned in The Guardian article, we see some differences:
CFBLNet/NATO:USA, GBR, CAN, FRA, DEU, ITA, NLD, NOR, ESP
The Guardian:USA, GBR, CAN, AUS, NZL, FRA, DNK, NLD, NOR
From the European NATO countries, France, The Netherlands and Norway are in both lists. The Guardian adds Denmark and the non-NATO members of the Five Eyes, which leaves Germany, Italy and Spain out.
Especially Germany and Italy not being included in this apparently close alliance seems strange, as both countries participate in other coalition groups and are both considered to be 3rd party partners of NSA. Maybe this explains Germany being "a little grumpy at not being invited to join the 9-Eyes group" as The Guardian read in GCHQ documents.
Unfortunately, The Guardian failed to provide any context or even a time period for their 9-Eyes and 14-Eyes listings, which makes it quite difficult to find an explanation for the different membership countries of these groups.
At first sight it seems there are two different 9-Eyes groups: one apparently closely related to NSA, and another one as a sharing group in the CFBLNet environment. But as 9-Eyes is used as a handling instruction for classified information, it has to be perfectly clear to which group of countries information marked REL 9-EYES may be released. Therefore we have to assume there can be only one 9-Eyes group at a time.
The 9-Eyes NATO group of the CFBL network was first mentioned in 2008 and still comprised the same nations in 2012. In the meantime, Sweden also became a full member of CFBLNet, but not being a NATO member, it wasn't included in the 9-Eyes sharing group.
![]() The CFBLNet countries in 2009, with three of the Five Eyes countries (yellow line),
The CFBLNet countries in 2009, with three of the Five Eyes countries (yellow line),
six European NATO countries and the NATO organization (black line),
six NATO guest nations (dotted line) and two non-NATO countries.
(source: NATO Education and Training Network (pdf), 2012) One option to explain the differences between the two 9-Eyes could be changing membership, with countries added or removed on an annual basis depending on their participation in the CFBLNet. But this also wouldn't fit with the Guardian's list, as Australia and New Zealand are no NATO-members and Denmark is not a fully participating member nation of the CFBL network.
Unless The Guardian misinterpreted the Snowden-documents, it seems quite unlikely that their 9-Eyes could be the same as the NATO 9-Eyes on the CFBL network, but it seems also unlikely that there are two groups called 9-Eyes at the same time. The best guess at this moment would be that the Guardian's 9-Eyes was a group that only existed somewhere before the NATO group was formed.
There's also the Multinational Interoperability Council (MIC), which is a forum for identifying interoperability issues and articulating actions to enhance coalition operations. It started in 1999 as the Six Nation Council and now has seven members: the US, Canada, Australia, Britain, France, Germany and Italy. It might be this group which is called7-Eyes.
Also interesting is Alliance Base, which was the cover name for a secret Counterterrorist Intelligence Center (CTIC) that existed between 2002 and 2009. It was based in Paris and was a cooperation between six countries: the US, Canada, Australia, Britain, France and Germany. There's no indication this group was designated by a number of 'Eyes'.
The 14-Eyes and 3rd and 4th party partnersNow let's take a look at the 14-Eyes community, which was revealed for the first time by The Guardian. Looking at the number and the participating countries, it comes very close to CFBLNet, which had 13 full members (12 nations + the NATO organization) since 2010. But there are also some differences again:
CFBLNet members:USA, GBR, CAN, AUS, NZL, FRA, DEU, NLD, NOR, ESP, ITA, SWE
The Guardian:USA, GBR, CAN, AUS, NZL, FRA, DEU, DNK, NLD, NOR, ESP, ITA, BEL, SWE
These lists are very similar, except that Denmark and Belgium, which are on the Guardian's list, are not a (full) member of CFBLNet. Maybe these two countries joined CFBLNet only very recently, and in that case the 14-Eyes could refer to this group. It does show though that these NATO countries (and Sweden) are cooperating in additional information-sharing initiatives.
The exact purpose of such a cooperation in the 14-Eyes group isn't clear. The New York Times only says that the nations comprising the 9-Eyes and 14-Eyes groups have formal arrangements with NSA, which is something that also makes a country a traditional 3rd party partner.
According to Snowden-documents, about 30 countries have this status, but so far only the names of Germany, France, Austria, Denmark, Belgium and Poland were
published. Some
othersources say that Norway, Italy, Greece, Turkey, Thailand, Malaysia, Singapore, Japan, South-Korea, Taiwan, Israel and South Africa are 3rd party partners too.
If we compare this to the 14-Eyes, we see that only France, Germany, Norway, Italy, Belgium and probably Spain are known 3rd party partners. Sweden, Denmark and The Netherlands are not, but it's
assumed they had or have less formal arrangements for exchanging raw and finished SIGINT and cryptologic information with NSA. This also applies to Finland and Taiwan, and therefore these countries are sometimes called 4th party partners.
It seems there are roughly three possibilities:
A. All countries of the 14-Eyes (and subsequently those of the 9-Eyes) are actually 3rd party partners, because of having formal arrangements with NSA. Which means Sweden, Denmark and The Netherlands must have acquired that position in recent years. Grouping them in two 'Eyes' would only make sense if that's for some specific initiatives.
B. Countries belonging to the 9-Eyes and 14-Eyes have a more close relationship with NSA and are therefore somewhere in between the 2nd party and the 3rd party nations. This is what both papers suggest, but it seems not very likely that relationships like these allow that much of (formal) refinement.
C. The 9-Eyes and 14-Eyes are groups created for specific goals and consist of the Five Eyes with some additional 3rd and 4th party nations, depending on whether their participation is needed for achieving those goals.
In 2010, France was
apperently ready to join the Five Eyes, but at the last moment the Obama White House said no.
The CFBL NetworkThe
Combined Federated Battle Laboratories Network (CFBL or CFBLNet) is a distributed Wide Area Network (WAN), which allows for the testing of new multinational information-sharing capabilities before they're transitioned to the actual operational networks which are used worldwide to support Combatant Command operations. CFBLNet enables the sharing and exchange of information on experimentation and interoperability testing.
Each member nation operates several "Battle Lab" sites which are hook into the CFBLNet backbone at a national Point-of-Presence (PoP). In 2012 there were 247 sites divided over 12 countries. The backbone traffic is secured with
TCE621 (in Europe) and
TACLANE E100 (or KG-175 in the US) network encryptors. The Multinational Information Sharing Program Management Office (MNIS PMO) maintains day-to-day control and coordination of the network.
Every year, also several other NATO countries participate or observe as guest nations in one or more CFBLNet initiatives at existing lab sites.
The CFBLNet grew out the network designed to support the US
Joint Warfighter Interoperability Demonstrations (JWID), which used to build a support network for the period of the demonstrations and tear it down afterwards. In 1999, the JWID exercise used, for the first time, a permanent infrastructure that became what is now called the Combined Federated Battle Lab Network (CFBLNet), as established by the NATO Consultation, Command and Control Board (NC3B) in 2001.
The 6, 8 and 10 EyesCreating separate access groups for coalition operations, and describing them with a certain number of 'Eyes' can be traced back to the early years of this century. The first occasion seems to have been the Joint Warrior Interoperability Demonstration 2003 in which also non-traditional partner countries were added to the communications network used by the UKUSA and NATO coalition.
Information sharing between different groups of coalition partners required that separate domains had to be created within one network: in 2003, the 5-Eyes countries and the NATO organization comprised the
6-Eyes domain, while these six members plus four Pacific Rim nations (Japan, South Korea, Thailand and Singapore) comprised the
10-Eyes domain. Each domain had its own Type-2/3DES-encrypted Virtual Private Network (VPN) which ran over a network secured by classified Type-1 encryption algorithms.
The 2004 edition of the Joint Warfighter Interoperability Demonstration also involved South-Korea, officially known as the Republic of Korea (ROK). To this end, three separate domains within CFBLNet were created and organized into two classification levels named 6-Eyes and 8-Eyes. The
8-Eyes domain consisted of the 6-Eyes countries plus NATO and ROK. The ROK domain was cryptographically
isolated from the rest of CFBLNet by using
TACLANE encryptors with Type-1 algorithms.
The 5, 4 and 3 EyesThe long-standing and close intelligence-sharing community of the Five Eyes was
downsized on two occasions. First in 1985, when New Zealand
refused US nuclear-armed or nuclear-powered ships to visit its ports. As a result, the island was cut out of most intelligence arrangements led by the US. Some SIGINT was still being shared, but New Zealand got no American HUMINT or military intelligence anymore, except for operations in which it's actually participating.
Things not to be shared with New Zealand, were
4-Eyes only now. Staying outside most of the allied military operations, New Zealand was also not connected to the CENTRIXS Four Eyes (CFE) network, which was created in 2001 and is extensively used for operational coordination between the remaining four partners: Australia, Canada, Great Britain and the US. Information restricted to these 4-Eyes partners is marked with their respective country codes or the abbreviation thereof: ACGU.
![]() A document showing the REL TO USA ACGU marking (source)
A document showing the REL TO USA ACGU marking (source)
For collaborative planning at the strategic level there's another network called Pegasus (until 2010: GRIFFIN), which provides secure e-mail, chat and VoSIP communications for the 5-Eyes partners, as the military cooperation between the US and New Zealand was restored again in 2007.
Another sub-group of the Five Eyes was formed when Canada didn't join the US in the 2003 war against Iraq. With New Zealand also not formally engaging, the 5-Eyes were now reduced to just
3-Eyes: the United States, Great Britain and Australia.
The relationship between these three countries became closer as both Britain and Australia were granted an upgrade of their intelligence access by president George W. Bush. For Example, both countries were granted (temporary and limited)
access to America's classified
SIPRNet for certain joint missions. This also reflects their bigger SIGINT collecting capabilities, compared to those of Canada and New Zealand.
CENTRIXS networksThe main US-led multinational coalition networks are called
CENTRIXS, which stands for Combined ENTerprise Regional Information eXchange System. It's a secure wide area network (WAN) architecture, which can be established according to the demands of a particular coalition exercise or operation. CENTRIXS supports intelligence and operations information sharing at the SECRET REL TO [country/coalition designator] level. Some important CENTRIXS networks are:
-
CENTRIXS Four Eyes (CFE) for the US, Britain, Canada and Australia.
-
CENTRIXS-J for the United States and Japan.
-
CENTRIXS-K for the United States and South-Korea.
-
CENTRIXS-ISAF (CX-I) which is the US component of the Afghan Mission Network to share critical battlefield information among 50 coalition partners.
-
CENTRIXS-GCTF (CX-G) is the US coalition network in Afghanistan to share information among more than 80 Troop Contributing Nations.
The countries connected to CENTRIXS-ISAF can be recognized as the
41-Eyes of the allied coalition in Afghanistan mentioned by The Guardian. This group grew slowly and was called
43-Eyes in 2010, when the NATO exercise Empire Challenge 2010 (EC10) changed its "main participating security domain" to "an International Security Assistance Forces (ISAF) equivalent 43-Eyes domain".
Probably also because of the steadily increasing number of coalition partners, shareable information is not marked with REL [..] EYES anymore, but with REL ISAF and REL GCTF.
ConclusionWe have seen that designations consisting of a number of 'Eyes' are used as a dissemination marking or handling instruction showing among which group of countries specific military or intelligence information may be shared.
The Guardian and the New York Times listed various 'Eyes' and some other groups in a way that suggests a hierarchy of how close their relationship with NSA would be: first the Five Eyes community, followed by 9-Eyes, 14-Eyes, NACSI, and with the 41-Eyes Afghanistan coalition being the loosest kind of cooperation.
A scheme like this looks attractive, but is at least partially misleading. For sure the Five Eyes are cooperating in the closest way, but the other groups have different scopes. NACSI is more like an advisory working group of NATO than an alliance of signal intelligence agencies, and the 41/43-Eyes community is for sharing battlefield information between members of the Afghanistan coalition.
Regarding the 9-Eyes and 14-Eyes communities, it's now up to journalists who have access to the Snowden-documents to provide more detailed information about whether they really represent more close alliances with NSA, or whether they're just 'working groups' of selected 3rd and 4th party nations, like most of the other 'Eyes' communities.
Summary of all known 'Eyes'- 3-Eyes: USA, GBR, AUS
- 4-Eyes: USA, GBR, CAN, AUS (ACGU)
- 5-Eyes: USA, GBR, CAN, AUS, NZL (FVEY)
- 6-Eyes: USA, GBR, CAN, AUS, NZL, NATO
- 7-Eyes: USA, GBR, CAN, AUS, FRA, DEU, ITA (MIC?)
- 8-Eyes: USA, GBR, CAN, AUS, NZL, NATO, ?, South-Korea
- 9-Eyes: USA, GBR, CAN, FRA, DEU, ITA, NLD, NOR, ESP (CFBLNet)
- 9-Eyes: Five Eyes + FRA, DNK, NLD, NOR (Guardian)
- 10-Eyes: USA, GBR, CAN, AUS, NZL, NATO, Japan, South-Korea, Thailand, Singapore
- 14-Eyes: Five Eyes + FRA, DNK, NLD, NOR, DEU, ESP, ITA, BEL, SWE (Guardian)
- 41-Eyes: ISAF-countries in ? (Guardian)
- 43-Eyes: ISAF-countries in 2010
Links and Sources- DailyDot.com: How the NSA ranks its international spying partners
- Disa.mil: Multinational Information Sharing (MNIS)
- Article in French about Empire Challenge 2008
- About Canada and the Five Eyes Intelligence Community (pdf)
- Far-Reaching Scenario Reflects Changing World (2003)
- Combined Operations Wide Area Network (COWAN)/Combined Enterprise Regional Information Exchange System (CENTRIXS) (pdf)




































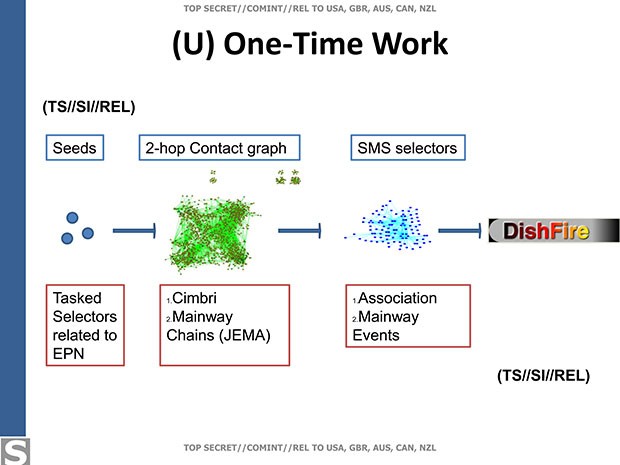







 COMINT (SI)
COMINT (SI)

















 For secure communications, the SecuSUITE application is added by inserting a
For secure communications, the SecuSUITE application is added by inserting a